Introduction
Businesses must protect their customers’ personally identifiable information (PII) and comply with data privacy laws to avoid legal and financial penalties. For companies, especially those lacking legal support, understanding data protection principles and adopting a structured compliance approach is crucial. This article serves as a guide for achieving PII compliance by detailing essential steps like conducting PII inventories and implementing strong security measures in an evolving regulatory landscape.
Understanding PII
Personally Identifiable Information (PII) is any data that can identify an individual, including names, addresses, social security numbers, and biometric data. PII is divided into sensitive (requiring strict protection) and non-sensitive (requiring some protection but less stringent). Organizations must understand PII to comply with data protection regulations like GDPR and CCPA, which call for security measures such as data encryption, access controls, and regular audits. This understanding helps organizations implement effective security measures to protect sensitive data and prevent breaches.
How to Ensure PII Compliance
To ensure compliance with Personally Identifiable Information (PII) regulations, businesses must understand key laws, including GDPR, CCPA, and HIPAA, as non-compliance can incur heavy penalties. Staying updated on regulatory changes is essential. AI technologies can support compliance by automating monitoring and alerting for potential violations. Additionally, effective data management practices, such as data mapping, are crucial for identifying, managing, and mitigating compliance risks.
Establishing Comprehensive Data Protection Protocols
Securing PII requires protective measures against unauthorized access and data breaches. Key strategies include robust encryption for data security during transmission and storage, secure storage to shield sensitive information, sophisticated access controls to limit access to necessary personnel, and multi-factor authentication (MFA) to enhance security against unauthorized users.
Conducting Detailed Data Assessments
Organizations must conduct thorough evaluations to identify and categorize personal data in their systems. This includes mapping data flows, assessing collection and storage methods, and recognizing system vulnerabilities. A detailed inventory of personally identifiable information (PII) enables targeted protection strategies and efficient resource allocation for high-risk areas. Data subject access requests (DSARs), integral to laws like GDPR and CCPA, affirm individuals’ rights to manage their personal data. To maintain compliance, businesses should develop a cohesive data governance strategy that incorporates data collection policies, management practices, retention schedules, and regular audits. By embedding compliance within their culture, organizations can foster a shared responsibility for data privacy across all departments. For organizations managing personal data in Switzerland, following a checklist for FADP compliance is also essential.
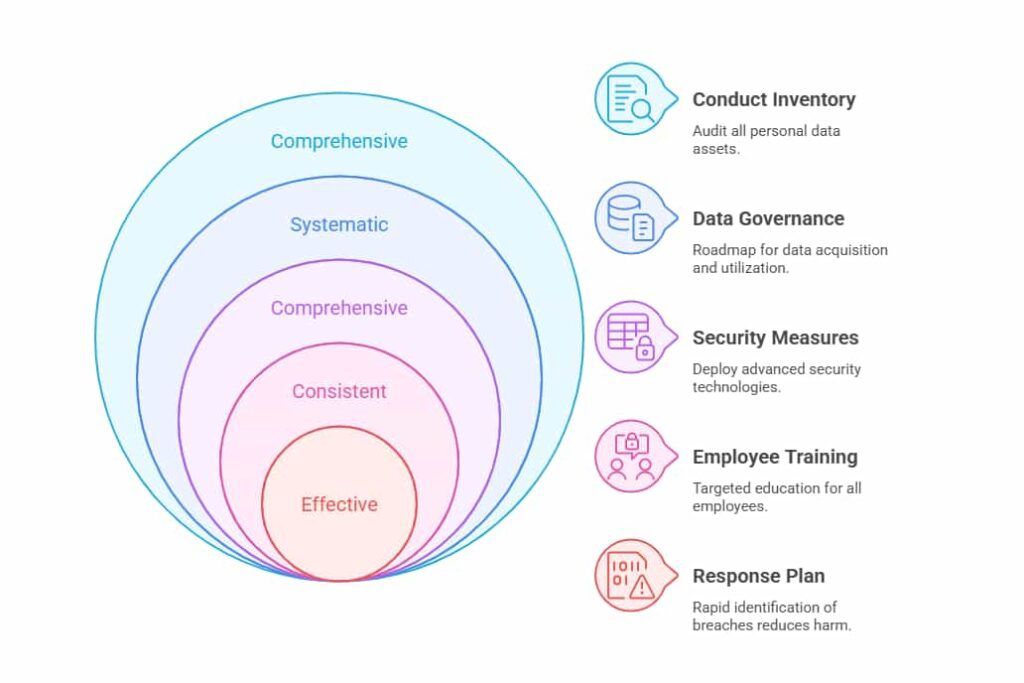
Step 1: Conduct a PII Inventory
Initiating a robust PII compliance strategy requires an in-depth audit of all personal data assets within the organization. Begin by cataloging every piece of personally identifiable information collected through various channels, ensuring that no data entry point—whether digital forms, customer service interactions, or third-party partnerships—remains unchecked. This meticulous process provides a comprehensive overview of the organization’s data architecture, forming a foundation for effective data governance.
Following identification, the classification of data by sensitivity is essential to tailor protection measures appropriately. To effectively protect data, it is crucial to classify PII, understanding its various locations and uses within the organization. Sensitive information, such as financial credentials or medical records, demands heightened security protocols compared to less critical data categories. This classification process should align with regulatory definitions and internal policies to maintain consistency. Leveraging advanced data management tools can streamline this task, offering precise real-time categorization and enhanced oversight.
Maintaining an accurate PII inventory is pivotal for regulatory compliance and effective data management. A well-documented data registry facilitates the implementation of robust access controls and data minimization techniques, thereby mitigating the risk of data breaches and unauthorized access. Regular reviews and updates of the inventory are vital to adapt to evolving data practices and regulatory landscapes. This proactive approach ensures that the organization remains agile in addressing new compliance demands and fortifying its data security posture.
Step 2: Develop a Comprehensive Data Governance Framework
Creating an effective data governance framework is fundamental for ensuring PII protection and aligning with legal mandates. This framework operates as a roadmap for systematic data management, covering elements such as data acquisition, utilization, preservation, and elimination. A thoughtfully crafted governance model not only shields sensitive information but also enhances operational efficiency by embedding compliance within the organizational ethos. Additionally, adhering to data processing principles is crucial, as they provide foundational guidelines for developing PII policies and ensuring lawful, transparent, and necessary data processing.
Crafting Detailed Data Management Protocols: To optimally manage PII, organizations must design specific protocols that outline data management processes at every juncture. This involves setting stringent access restrictions, ensuring only designated personnel handle sensitive information, and establishing timelines for data retention that dictate the duration data remains in storage before its secure disposal. These protocols provide a solid foundation for uniform data management practices, ensuring personnel are well-informed about their duties in safeguarding PII. Furthermore, adhering to industry standards during periodic audits and compliance reviews is essential to ensure that businesses are following PII regulations and fostering a culture of privacy and data protection.
Deploying Advanced Oversight Mechanisms: In light of the dynamic nature of privacy laws, implementing robust oversight mechanisms is crucial to maintaining alignment with compliance requirements. By utilizing sophisticated oversight tools, organizations can achieve continuous visibility into data processing activities, swiftly identifying any compliance issues or security breaches. These tools enable proactive risk mitigation, allowing businesses to promptly address discrepancies and uphold the robustness of their governance framework.
Integrating these components into a unified governance strategy necessitates cross-departmental collaboration, fostering a culture of transparency and accountability. Routine evaluations and refinements of the governance framework ensure its ongoing relevance and efficacy in managing emerging data privacy challenges. By prioritizing a structured approach to data governance, companies can strengthen their defense against regulatory challenges and affirm their dedication to customer data protection.
Step 3: Implement Data Security Measures
Securing personally identifiable information (PII) requires a comprehensive approach that includes deploying advanced security technologies and protecting sensitive data. A key element of this strategy is the use of data masking—a technique that obscures sensitive information by replacing it with fictional data. This process ensures that the actual data remains undisclosed even if accessed by unauthorized individuals. By implementing data masking both during data processing and storage, organizations can effectively shield PII from exposure, thereby maintaining confidentiality and compliance with privacy standards.
Utilizing Advanced Access Management Protocols: Enhancing security further involves implementing sophisticated access management systems. Role-based access control (RBAC) restricts data access based on an individual’s role within the organization, ensuring that only those with a legitimate need can view or manipulate PII. This method minimizes the potential for insider threats by limiting data access to essential personnel only. Moreover, implementing context-aware access controls, such as location and time-based restrictions, adds an additional layer of security, ensuring that data can only be accessed under predefined conditions.
Deploying Behavioral Analytics Tools: Complementing traditional security measures, behavioral analytics tools offer real-time insights into user activities, identifying anomalies that may indicate potential security breaches. These tools analyze patterns in data access and usage, allowing organizations to detect suspicious behavior that deviates from established norms. By monitoring these patterns continuously, companies can swiftly respond to emerging threats, reducing the risk of unauthorized data access and ensuring the integrity of PII. This also helps in preventing risks such as identity theft.
Through the integration of these advanced data security measures, organizations can establish a robust defense against a variety of potential threats. This multi-layered security framework not only fulfills regulatory requirements but also reinforces the organization’s dedication to safeguarding data privacy, thereby enhancing stakeholder trust and confidence.
Step 4: Train Employees on Data Protection Best Practices
Cultivating a culture of security within an organization requires consistent and targeted education for all employees. Regular training sessions ensure that staff understand the latest developments in PII compliance and the specific roles they play in safeguarding sensitive information. These sessions should provide in-depth coverage of current regulatory changes, data handling procedures, and the potential consequences of failing to comply with data protection standards, ensuring that employees are fully equipped to integrate these practices into their daily operations. Emphasizing the importance of PII compliance measures, such as proactive employee training programs, ensures that staff are well-versed in these measures and can effectively implement them.
Designing Tailored Training Modules: Crafting training programs that cater to the distinct needs of various departments helps ensure that each team receives pertinent and actionable insights. For example, sales teams should focus on secure customer interactions, while IT staff might require more technical training on security protocols. Incorporating hands-on activities such as simulated data breach scenarios and interactive workshops enhances engagement, helping employees apply data protection strategies effectively in their roles.
Measuring Training Effectiveness: Establishing clear metrics to evaluate the success of training initiatives is crucial. Regular evaluations, such as knowledge assessments or practical demonstrations, can pinpoint areas needing further attention and guide future training enhancements. Keeping detailed records of training participation and outcomes ensures accountability, reinforcing an organization’s dedication to continuously advancing its data protection initiatives.
By embedding a mindset of shared responsibility for data security, organizations can significantly mitigate risks associated with data breaches and ensure compliance. Providing employees with the skills and knowledge necessary to protect PII strengthens overall security measures and enhances trust with clients and partners.
Step 5: Establish a Response Plan for Data Breaches
Crafting an effective incident response plan for data breaches is a critical component of safeguarding PII. Rapid identification of breaches reduces potential harm, allowing organizations to respond efficiently. Implementing advanced detection systems that offer continuous monitoring and instant alerts is essential. These systems should be adept at identifying irregular patterns that signify unauthorized access, enabling swift action to prevent further data exposure.
A robust incident response plan is necessary to effectively address data breaches, enabling organizations to quickly respond to unauthorized access and mitigate damage.
Designing a Comprehensive Reporting Structure: A well-defined reporting mechanism is vital in managing data breach scenarios. Organizations must delineate a clear protocol for both internal and external reporting, identifying key individuals responsible for breach management and outlining the escalation process. Employees should have a clear understanding of the contact points and the specific information required when reporting a breach. This approach ensures timely notification to all involved parties, facilitating a coordinated response to the incident.
Building Effective Communication Channels: Post-breach communication with affected individuals and regulatory bodies is crucial. Transparency in these communications underscores the organization’s dedication to resolving the breach responsibly. A predefined strategy should outline the steps for notifying affected parties, including the mode, timing, and content of the communications. This strategy must align with legal mandates, providing clarity on the breach’s extent, compromised data, and remedial measures being undertaken. Clear and consistent communication helps maintain trust and mitigates reputational damage.
By meticulously developing a thorough response plan, businesses can effectively manage the intricacies of data breaches and reaffirm their commitment to comprehensive data protection. Such preparedness not only ensures compliance with privacy laws but also strengthens the organization’s standing as a reliable steward of customer information.
Tips on Maintaining PII Compliance

1. Regularly Review and Update Policies
Ensuring the resilience of PII compliance involves establishing a dynamic policy framework that adapts to evolving data protection landscapes. Organizations must institute a periodic review process that scrutinizes existing policies to identify areas susceptible to emerging threats and regulatory modifications. This iterative process is vital to maintaining robust data governance, ensuring that all protective measures are current and effective. Additionally, understanding the importance of cross-border data transfers is crucial for compliance with international regulations and avoiding significant fines and reputational damage.
Collaboration with cross-functional teams during policy assessments enriches the understanding of practical data-handling challenges faced across departments. By integrating insights from IT, legal, and operational teams, policy updates can be more accurately tailored to address specific organizational needs, thereby enhancing the overall security posture and fostering a culture of proactive compliance.
2. Utilize Automated Tools for Data Monitoring
Incorporating advanced automated solutions into data management practices is essential for ensuring continuous oversight of PII data. These tools offer sophisticated capabilities for tracking data usage and interactions, allowing for immediate identification of activities that deviate from compliance standards. Automated systems not only streamline the monitoring process but also enhance the accuracy and efficiency of compliance efforts.
These technologies provide real-time data visibility, enabling swift corrective actions when anomalies or potential breaches are detected. By automating the generation of detailed audit logs, organizations can maintain comprehensive records that support transparent reporting and facilitate regulatory audits. This strategic deployment of technology is crucial for sustaining a high level of data protection and reinforcing the organization’s commitment to safeguarding personal information.
Conclusion
Ensuring PII compliance is an ongoing process that requires vigilance, adaptability, and a proactive approach to protect data. By following these key steps and incorporating best practices into your organization’s data management strategies, you can effectively navigate the complexities of regulatory compliance and safeguard your customers’ sensitive information. If you’re looking for a comprehensive solution to streamline your Shopify store’s compliance with GDPR and other privacy regulations, we invite you to try Pandectes for free and experience the peace of mind that comes with robust data protection. Sensitive data protection is crucial to ensure compliance with privacy laws and standards, and regular audits and reviews are essential to uphold these requirements.