Introduction
Vendor Risk Management is crucial for companies that work with third-party vendors or suppliers. The process involves identifying and assessing vendors, categorizing them based on risk, and implementing appropriate risk treatment measures. Establishing a vendor oversight framework involving different stakeholders and conducting periodic reviews is essential to ensure effectiveness and alignment with strategic objectives. A proactive approach to Vendor Risk Management can minimize the potential risks associated with vendor relationships and safeguard a company’s operations, finances, reputation, and compliance.
Why is Vendor Risk Management important?
Vendor risk management is vital in safeguarding an organization’s operations, reputation, and sensitive information. By implementing a robust vendor risk management program, companies can:
Identify and assess vendor risks
To ensure the smooth functioning of their operations, organizations must be proactive in identifying and assessing the potential risks associated with their vendors. A structured vendor risk management process is a key tool that can be used for this purpose.
This process involves a thorough evaluation of various factors, including cybersecurity risks, financial risks, reputational risks, legal or compliance violations, and any threats that may hinder business continuity. By implementing such a process, organizations can mitigate the risks associated with their vendor relationships and ensure they can maintain high quality and efficiency in their operations.
Mitigate risks and ensure compliance
Organizations must prioritize understanding these risks in depth to manage and mitigate vendor risks effectively. This can be achieved by implementing robust security controls to identify and mitigate potential vulnerabilities. Additionally, it is crucial to ensure that vendors comply with all relevant regulatory standards, as this can provide an added layer of protection against potential risks.
Finally, creating a comprehensive vendor risk management framework that aligns with industry best practices can help organizations stay ahead of potential risks and ensure that they are well-prepared for any challenges that may arise. By prioritizing these key strategies, organizations can effectively manage vendor risks and protect their assets and reputation in the long term.
Protect customer data
As a responsible organization dealing with sensitive customer information, it is imperative to acknowledge that vendors may have access to such data. However, any security protocol failures on their part could potentially lead to data breaches, which is why it is crucial to implement vendor risk management strategies.
Such measures help ensure adequate data security protocols are in place and customer data is safeguarded against any potential threats. By being proactive in this regard, organizations can avoid costly and damaging data breaches that could harm their reputation and bottom line.
Enhance vendor relationships
A proactive approach to managing vendor risk can be incredibly advantageous for organizations. By doing so, they can establish clear expectations with their vendors, including service level agreements and regular assessments. This helps strengthen the vendor relationship and fosters a greater sense of trust and collaboration between organizations and their vendors. Ultimately, this can lead to better outcomes for everyone involved and help ensure that all parties work towards the same goals.
Vendor Risk Management process
When it comes to vendor risk management, several important steps must be followed to ensure your organization’s safety and security. These steps typically involve a careful and thorough assessment of the vendor in question, including evaluating their track record, reputation, and overall level of risk. Additionally, it may be necessary to conduct regular audits, reviews, and assessments to ensure ongoing compliance and minimize the risk of any potential issues or threats. Ultimately, by following these steps and taking a proactive approach to vendor risk management, organizations can help safeguard their operations and protect themselves against potential harm or liability.
Vendor inventory
Maintaining a thorough record of all the vendors or third-party associations that the organization has is of paramount importance. This can be achieved by creating a comprehensive list that incorporates relevant details such as the nature of the relationship, the precise services offered, and any potential risks associated with the association. Organizations can manage vendor or third-party relationships by keeping track of these crucial details and ensure everything runs smoothly.
Vendor risk assessment
To ensure comprehensive vendor risk management, it is highly recommended to conduct thorough vendor risk assessments. This process involves a meticulous evaluation of various factors that could pose risks, such as cybersecurity risks, financial stability, regulatory compliance, and the overall risk potential of the vendor. By conducting this assessment, organizations can better understand and mitigate potential risks associated with their vendors, ultimately safeguarding their business operations and reputation.

Risk mitigation strategies
In order to ensure that risks are managed efficiently and effectively, it is imperative to develop personalized risk mitigation strategies for each vendor that consider their particular risk profile. These strategies may involve implementing appropriate security measures, establishing vendor compliance guidelines, and creating customized vendor risk management programs tailored to the specific needs of each vendor. Businesses can better protect themselves against potential risks and safeguard their operations and reputation by taking these steps.
Ongoing monitoring
Maintaining a watchful eye on vendors’ performance and risk exposure throughout their partnership with your organization is of utmost importance. To achieve this, it is essential to carry out regular assessments and periodic audits while keeping the lines of communication open to ensure compliance with security measures and contractual obligations. By doing so, you can effectively manage the risks associated with vendor relationships and safeguard the integrity of your organization.
Incident response and remediation
In order to maintain a secure and reliable vendor ecosystem, it is imperative to establish comprehensive protocols for incident management and breach response. These protocols should encompass clear guidelines for communication, remediation, and incident response procedures to minimize any security breaches’ potential impact. By implementing these processes, organizations can effectively address any incidents that may arise and ensure the safety and integrity of their vendor partnerships.
Best practices for effective Vendor Risk Management
To effectively manage vendor risk, businesses should consider implementing the following best practices: thoroughly vetting potential vendors before engagement, conducting regular risk assessments of active vendors, establishing clear contractual expectations and requirements, monitoring vendor performance and compliance, and having a plan in place for addressing any identified issues or breaches. By following these guidelines, organizations can mitigate potential risks and ensure the safety and security of their operations.
Vendor selection process
It is highly recommended that an effective vendor selection process be implemented, which entails conducting comprehensive due diligence and risk assessments before bringing on board any new vendors. This approach ensures that potential risks are identified and dealt with promptly right from the beginning of the collaboration. A well-thought-out vendor selection process also helps establish a strong and mutually beneficial partnership with the vendor, ultimately leading to better outcomes for both parties involved.
Vendor Risk Management strategy
Developing a comprehensive vendor risk management plan is crucial for any organization. To ensure alignment with the overall risk management framework, the plan should accurately outline the levels of risk that the organization is willing to accept. It should also clearly define the measures that will be taken to mitigate those risks and the processes that will be employed to monitor them over time continuously.
By doing so, the organization can effectively identify, assess, and manage any potential risks associated with vendor relationships. Ultimately, this will enable the organization to operate with increased confidence and security while minimizing any potential negative impact on its operations and reputation.
Vendor relationship management
Building a solid and transparent relationship with vendors is paramount for any organization. In order to achieve this, it is imperative to maintain regular communication with them. This helps keep each other informed about updates or changes and fosters collaboration and mutual respect.
In addition, conducting periodic assessments of the vendor’s performance is crucial to ensure that they meet the organization’s standards and expectations. This helps establish a safe and reliable partnership based on trust, transparency, and accountability. By working with vendors in this manner, organizations can achieve their goals while building lasting relationships that benefit both parties.
Automate Vendor Risk Management
Businesses can effectively utilize technology and vendor risk management platforms to streamline and automate the vendor risk management process. This not only enhances the efficiency of the process but also facilitates real-time monitoring of vendor-related risks. Additionally, this approach offers businesses greater insight into the potential risks associated with their vendors and enables them to make informed decisions when selecting and managing vendors. By adopting this approach, businesses can effectively mitigate risks and protect their operations from potential disruptions and financial losses.
Training and awareness
To ensure that vendor risk management is implemented effectively, it’s crucial to educate employees and stakeholders on the best practices. This encompasses raising awareness about possible risks, developing clear policies and procedures, and conducting training sessions to identify and handle vendor risks. By doing so, organizations can minimize the likelihood of disruptions caused by vendor-related issues and maintain a secure and trustworthy business environment.

VRM lifecycle and third-party risk management
The Vendor Risk Management (VRM) lifecycle refers to an organization’s structured process of assessing and managing risks associated with vendors and third-party relationships. It involves various stages and activities aimed at optimizing the vendor risk management program and protecting the confidentiality and integrity of the organization. Let’s delve into the details of the Vendor Risk Management lifecycle.
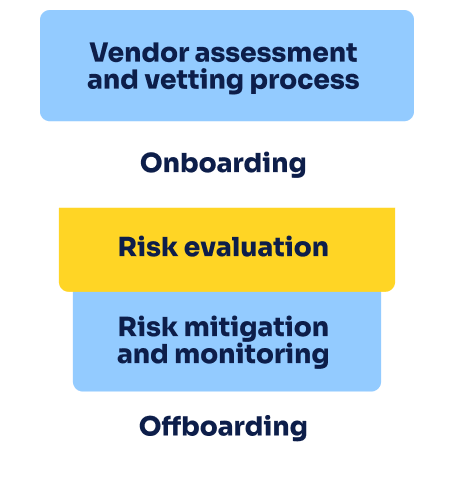
Vendor assessment and vetting process
The lifecycle begins with the assessment and vetting of vendors. Organizations evaluate potential vendors based on their capabilities, financial stability, security controls, compliance with regulations, and reputation. This stage aims to select vendors that align with the organization’s requirements and risk tolerance.
Onboarding
Once vendors are selected, the onboarding process begins. This involves establishing contractual agreements, defining service level agreements (SLAs), and clearly outlining expectations and responsibilities. The onboarding stage ensures vendors understand the organization’s risk management framework and compliance requirements.
Risk evaluation
The next phase of the lifecycle focuses on evaluating the risks posed by vendors. Organizations conduct comprehensive risk assessments, considering factors such as cybersecurity risks, financial stability, reputational risks, legal or compliance breaches, and potential business disruptions. This evaluation helps identify the level of risk associated with each vendor and prioritize risk mitigation efforts.
Risk mitigation and monitoring
Once risks are identified, organizations develop strategies to mitigate them. This involves implementing security controls, conducting due diligence checks, ensuring regulatory compliance, and defining vendor risk management programs tailored to each vendor’s risk profile. Ongoing monitoring and performance evaluations are crucial to track vendors’ adherence to agreed-upon security measures and contractual obligations.
Offboarding
The lifecycle concludes with the offboarding stage, which focuses on the end of a vendor relationship. This phase is as important as the onboarding process and includes contract termination, data handover, and vendor relationship closure. Proper offboarding ensures a smooth transition and minimizes potential risks associated with the termination of vendor services.
Conclusion
In the current landscape of globalized commerce, it is of utmost importance for enterprises to thoroughly comprehend and proficiently manage the risks associated with their vendors. One of the most effective ways to achieve this is by implementing a robust Vendor Risk Management program that proactively identifies, assesses, and mitigates potential risks arising from vendor relationships.
By establishing a structured Vendor Risk Management (VRM) process, businesses can assertively protect their operations, reputation, and confidential information while simultaneously fostering more secure and resilient vendor partnerships. This approach enables companies to avoid potential vendor-related risks and respond effectively to any issues that may arise, thereby reducing the overall exposure to inherent risks.