Introduction
Organizations increasingly rely on third-party vendors, suppliers, and business partners to deliver essential products and services in today’s interconnected business environment. While these third-party relationships can bring significant benefits, they also introduce substantial risks, including security breaches, data theft, and reputational damage. Effective third-party risk management (TPRM) is critical to managing these risks and protecting an organization’s financial and reputational interests. This article will overview third-party and supplier risk management, including critical phases, risk identification and assessment, risk mitigation strategies, and best practices.
What is third-party risk management (TPRM)?
Third-Party Risk Management (TPRM) describes identifying risk and minimizing it as an outcome of an outsourced service. Digital risks fall into a third-party category. They can be financial, environmental, public relations, or security concerns. This risk exists because the supplier has a right to access confidential data, personal information, or protected medical information. Because third parties provide essential support to business operations, third-party risk management has become an important element within all cybersecurity programs. Those who work for your organization are called third parties.
Why is third-party risk management critical?
The discipline grew with an increase in data breaches and incidents across industries and the reliance heavily on outsourcing. Disruptive situations can affect almost any business or third party, regardless of size and geographical position. Data breaches and cybersecurity incidents also occur. In 2021, outages or unauthorized incidents were shown to impact business resilience. Most modern companies depend on third-party services to run their operations effectively.
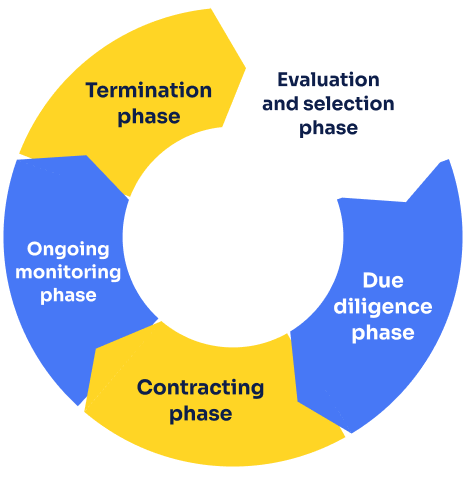
Key phases of third-party risk management
The TPRM process involves several key phases: evaluation and selection, due diligence, contracting, ongoing monitoring, and termination.
Evaluation and selection phase
The evaluation and selection phase of the supply chain involves identifying the third-party vendors, suppliers, and business partners essential to the organization’s business operations. During this phase, the organization must consider several factors, including the criticality of the third-party relationship, the inherent risk of the vendor, typical relationship, and the risk factors associated with the product or service.
Due diligence phase
The due diligence phase involves a comprehensive review of the third-party vendor, supplier, or business partner. This includes evaluating the vendor’s financial stability, security posture, and regulatory compliance. In addition, the organization must conduct a risk assessment to identify potential risks associated with the vendor’s product or service.
Contracting phase
The contracting phase involves negotiating and executing a contract with the third-party vendor, supplier, third-party network, or business partner. This contract should include key provisions related to TPRM, such as data protection requirements, security obligations, and reporting requirements. It should also outline the roles and responsibilities of both parties in managing third-party risks.
Ongoing monitoring phase
The ongoing monitoring phase involves continuously monitoring third-party relationships for emerging risks. This includes conducting regular risk assessments, maintaining detailed records of all third-party identification and third-party management activities, and implementing risk mitigation strategies to manage identified risks. Ongoing monitoring ensures that third-party risks are managed effectively and that the organization can respond quickly to emerging risks.
Termination phase
The termination phase involves ending the third-party relationship. This may occur for several reasons, including a breach of contract, emerging risks that cannot be effectively managed, or changes in the organization’s business operations. Organizations must have a plan in place to terminate third-party relationships, including procedures for transitioning to a new vendor, supplier, or business partner.

Third-party risks
Third-party risks vary significantly depending on the ongoing nature of the vendor’s product or service, industry, and location. Some common risk factors include:
Security risk
Security risk involves the risk of a data breach or unauthorized access to sensitive data. For example, a vendor that handles sensitive customer data may introduce significant security risks.
Financial risk
Financial risk involves the risk of financial loss or instability. For example, a vendor that provides financial services may have inherent risks related to financial stability.
Strategic risk
Strategic risk involves a vendor failing to meet the organization’s strategic objectives. For example, a vendor that provides critical products or services may introduce significant strategic risks if they are unable to meet the organization’s needs.
Operational risk
Operational risk involves the risk of disruption to business operations. For example, a vendor that provides critical products or services may introduce significant operational risks if they experience a service outage or other disruption.
Identifying and assessing third-party risks
Effective TPRM requires a comprehensive risk identification and assessment process. This process involves evaluating the risks associated with each third-party relationship, considering factors such as the inherent risk of the vendor’s risks, the criticality of the relationship, and ongoing risks.
Inherent risk assessments
Inherent risk assessments focus on evaluating the risks associated with the vendor and critical aspects such as financial stability, security posture, and regulatory compliance. This assessment is crucial to identifying potential risks associated with the vendor before entering into a third-party relationship.
Vendor’s inherent risk assessments
The vendor’s inherent risk assessments focus on the specific risks associated with the vendor’s product or service. For example, a vendor that provides software may have inherent cyber risks related to data security, while a vendor that provides financial services may have inherent risks related to financial stability. The vendor’s inherent risk assessment is critical to identifying potential risks associated with the vendor’s product or service.
Constant monitoring
Constant monitoring involves continuously monitoring third-party relationships for emerging risks. This includes conducting regular risk assessments and implementing risk mitigation strategies to manage identified risks. Continuous monitoring ensures that third-party risks are managed effectively and that the organization can respond quickly to emerging risks.

Risk mitigation strategies
Once risks associated with third-party relationships have been identified and assessed, the organization must implement risk mitigation strategies to manage these risks effectively. Common risk mitigation workflows include:
Implementing controls
Implementing controls involves implementing security controls to reduce the risk of a security breach or data theft. For example, the organization may require that the vendor encrypts sensitive data or implement two-factor authentication.
Maintaining a detailed evidence trail
Maintaining a detailed evidence trail involves documenting all third-party management activities, including due diligence, risk assessments, and ongoing monitoring. This documentation is critical to demonstrating compliance with regulatory requirements and responding to audits.
Consolidating vendor information
Consolidating vendor risk and information involves maintaining a centralized database of all third-party relationships. This database should include critical information such as vendor contact information, contract information, and risk assessment information. Consolidating vendor risk and information can help organizations manage third-party risks more effectively and respond quickly to emerging risks.
Managing fourth parties
Managing fourth parties involves managing the risks associated with new third parties or with vendors’ vendors. Fourth parties can introduce significant risks into the third-party ecosystem, and organizations must have a plan to manage these risks effectively.
Best practices for third-party risk management
Effective TPRM requires a comprehensive approach incorporating best practices for managing third-party risks. Some best practices include:
Assigning a risk owner
Assigning a risk owner is the first step in effective third-party risk management. This person is responsible for overseeing the entire third-party risk assessment and management program and ensuring that all parties involved are aware of their roles and responsibilities. The risk owner is typically a senior executive with authority over the relevant business areas.
Examples of responsibilities that may fall under the risk owner’s purview include:
Establishing and implementing third-party risk management policies and procedures
Approving new third-party relationships and vendor contracts
Assessing the inherent risk of third-party relationships and developing strategies for mitigating those risks
Ensuring ongoing monitoring and review of third-party relationships to ensure compliance with established policies and procedures
Maintaining a detailed evidence trail of all activities related to third-party risk management
Conducting initial due diligence
Once a risk owner has been identified, the next step is to conduct initial due diligence on potential third-party vendors. This includes gathering information about the vendor’s business practices, financial stability, security posture, and other critical factors.
Examples of steps that may be included in the initial due diligence process include:
Conducting a background check on the vendor to verify its identity and legal status
Reviewing the vendor’s financial statements and credit reports to assess its financial stability
Evaluating the vendor’s security posture and risk management capabilities
Checking for any past instances of data breaches or other security incidents
Assessing the vendor’s compliance with applicable laws and regulations
Evaluating and selecting third-party vendors
After conducting initial due diligence, the risk owner can evaluate supply chain risk management and select potential third-party vendors. This process involves assessing the vendor’s inherent risk and developing strategies for mitigating that risk.
Examples of factors that may be considered in the evaluation and selection phase include:
The nature and scope of the services provided by the vendor
The vendor’s security posture and risk management capabilities
The vendor’s financial stability and ability to deliver services over the long term
The vendor’s compliance with applicable laws and regulations
The vendor’s reputation within the industry and among its peers

Establishing a third-party risk management program
Once third-party vendors have been selected, the risk owner can establish a third-party vendor risk management program. This program should include policies and procedures for managing third-party risks throughout the vendor lifecycle.
Examples of components that may be included in a third-party risk management program include:
Ongoing monitoring of third-party relationships to ensure compliance with established policies and procedures
Regular assessments of third-party risks to identify emerging threats and vulnerabilities
Developing and implementing common risk mitigation workflows to ensure consistent and effective risk management practices across all third-party relationships
Maintaining detailed records of all activities related to third-party risk management to demonstrate compliance with applicable laws and regulations
Maintaining ongoing monitoring and review
Maintaining ongoing monitoring and review of third-party relationships is essential to effective third-party risk management. This includes regularly assessing the vendor’s security posture, financial stability, risk tolerance, and other critical factors to ensure ongoing compliance with established policies and procedures.
Examples of activities that may be included in ongoing monitoring and review include:
Regular security assessments of third-party vendors to identify potential vulnerabilities and threats
Periodic reviews of third-party contracts to ensure that they are still aligned with the organization’s risk management objectives
Reviewing the vendor’s compliance with applicable laws and regulations
Conducting regular audits of third-party relationships to identify and mitigate potential risks
Conclusion
Third-party management is critical to modern business operations, and organizations should not take it lightly. Managing third-party risk assessments and third-party risks requires a continuous and ongoing effort that involves several stages, including identification, evaluation and selection, due diligence, contract negotiation, monitoring, and termination.
The key to successful third-party vendor management has a comprehensive risk management program that incorporates all critical risks and maintains detailed records of all interactions with third-party vendors. It is also essential to understand that not all vendors pose the same level of risk, and the risk mitigation strategies should be tailored to each vendor’s inherent risk. Moreover, organizations should be aware of the potential risks that third-party relationships can bring, including cyber, reputational, and financial risks. To mitigate these risks, organizations should assess their third-party ecosystem regularly, consolidate vendor information, and prioritize critical vendors.
Eventually, the success of many organizations’ third-party management programs depends on the involvement of all stakeholders, including procurement teams, security teams, and business units. All parties should work together to ensure third-party relationships comply with regulatory requirements, maintain a robust security posture, and not disrupt business operations. By adopting a comprehensive and proactive approach to third-party management, organizations can minimize their exposure to third-party risks and ensure the sustainability of their business operations.