Managing Customer Data Requests has become a critical responsibility in today’s data-driven environment, especially with GDPR compliance at the forefront. This comprehensive guide provides IT experts with the technical strategies needed to efficiently handle customer data requests while safeguarding data security and ensuring compliance. By effectively managing these requests, organizations can enhance customer satisfaction and loyalty.
We’ll cover system architecture, workflows, and address challenges to ensure successful customer data management. Let’s dive into unlocking the secrets of customer data requests: A must-read guide for IT experts.
What is a Customer Data Request?

A Customer Data Request refers to any formal request made by an individual to access, modify, delete, or interact with their personal customer data stored by an organization. These requests are driven by regulations like GDPR, which grant individuals specific rights over their customer data, ensuring data privacy and enabling customer loyalty. Efficient handling of these requests is essential for maintaining customer satisfaction, improving the customer experience, and ensuring compliance with legal requirements.
By analyzing customer data, organizations can gain valuable customer insights that enhance marketing strategies and contribute to better business strategies. Timely and accurate responses to these requests help maintain a strong connection with customers, fostering customer engagement and customer satisfaction, and building trust, which ultimately boosts customer loyalty.
Types of GDPR Data Requests
Data Access: Subject access requests (SARs) allow individuals to view their personal data.
Data Rectification: Requests to correct inaccurate data.
Right to Be Forgotten: Requests to delete stored personal data.
Data Portability: Allows individuals to request their data in a machine-readable format like CSV or JSON.
System Architecture for Efficient Data Request Handling
Building a scalable, secure system is key to efficiently processing customer data requests. The architecture must ensure fast data retrieval, compliance with regulations like GDPR, and scalability as data volumes grow. These processes are essential for maintaining customer satisfaction and delivering a seamless customer experience.
Centralized Data Management
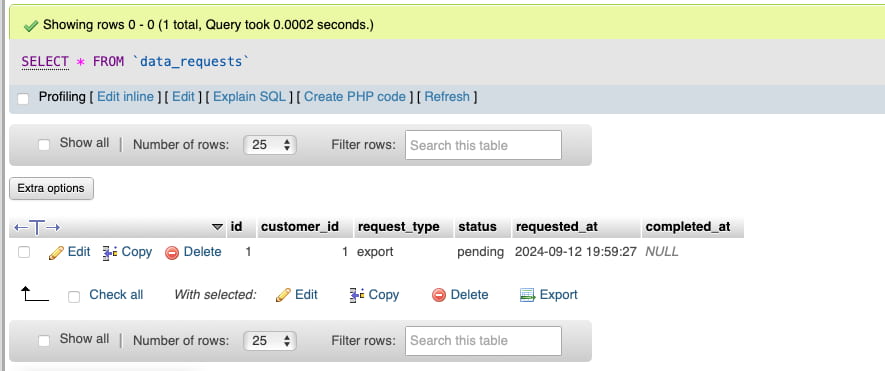
Centralizing your data in a single, well-structured database, such as PostgreSQL or MySQL, simplifies the retrieval process for data requests. For example, a single query like:
SELECT * FROM customer_data WHERE customer_id = '12345';Can instantly retrieve all relevant customer data, ensuring quick and accurate responses. This approach also facilitates better analysis of customer behavior, enabling businesses to gain valuable customer insights for more effective strategies.
By centralizing more data, you can make informed purchasing decisions and drive continuous improvement in business operations, leading to enhanced customer experiences. With this structure in place, organizations can improve effectiveness by leveraging data analytics to identify trends, personalize offerings, and refine marketing strategies.
Scalability and Microservices Architecture
Implementing a microservices architecture allows different types of requests (data access, rectification, deletion) to be handled independently. Each microservice can be scaled horizontally to handle high request volumes, ensuring your system can process thousands of requests without slowing down.
Data Security and Access Control
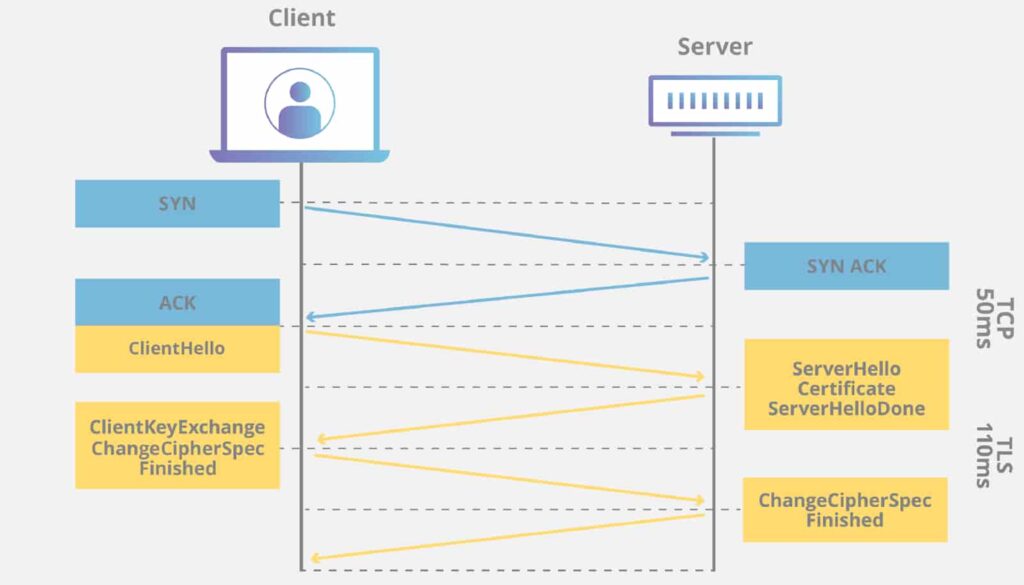
Data security is a critical component of maintaining both business operations and customer trust, particularly when dealing with big data and sensitive customer information. Implementing robust encryption protocols is essential to safeguard personalized offers and shopping experiences. Encryption should be enforced both in transit and at rest—using TLS (Transport Layer Security) for data in transit and AES-256 (Advanced Encryption Standard) for data at rest—to protect customer data across various business touchpoints.
In addition to encryption, strong access control mechanisms, such as Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA), are pivotal in restricting unauthorized access and ensuring that only authorized personnel can interact with sensitive data. This is an important element of protecting personalized experiences, ensuring that companies can offer unique shopping experiences while safeguarding data privacy.
These security measures also play a key role in improving business outcomes by ensuring compliance with regulations like GDPR, building consumer confidence, and enabling companies to maintain a competitive advantage. By utilizing advanced technology, businesses can enhance their data security framework to not only protect customer data but also optimize conversion rates and foster long-term customer loyalty.
Ensuring Data Integrity and Logging
Before any data modification or deletion, the system must validate data integrity through hash-based validation. Every action on customer data should be logged with an audit trail:
INSERT INTO audit_logs (action, user_id, data_before, data_after, timestamp) VALUES ('data_correction', '12345', '{old_data}', '{new_data}', NOW());This ensures traceability and compliance with GDPR regulations while providing valuable insights into customer behavior and helping to analyze customer data effectively.
Implementation Strategies for Automation
Automation is key to handling customer data requests at scale. Well-defined workflows can significantly reduce manual tasks, ensuring quick and accurate responses.

Automating Data Access Requests
Data deletion workflows can also be automated. Once a deletion request is verified, the system sends commands to all relevant data stores and logs the deletion in the audit trail. A RESTful API such as /delete-data can trigger these processes.
Automating Data Deletion Requests
Using job scheduling systems like Apache Airflow, organizations can efficiently handle data portability requests in batches. These processes involve generating export files for the customer to download securely, which enhances data management and customer experience.
By automating data deletion requests, organizations reduce manual tasks, ensure compliance with Data Regulations, and protect customer data. This approach not only saves time but also increases the efficiency of data handling, making it easier to maintain customer satisfaction and respond promptly to customer feedback and requests.
Automating Data Portability
Using job scheduling systems like Apache Airflow, data portability requests can be processed in batches, generating export files for the customer to download securely.
Overcoming Challenges in Customer Data Request Handling
Processing customer data requests efficiently comes with several challenges, particularly when dealing with large datasets, inconsistent data, and security risks. For example, in the retail industry, organizations must handle large volumes of historical data and raw data, which require advanced technology to manage and process efficiently.
Data scientists play a crucial role in identifying patterns within this data, helping to segment customers based on their preferences and ensure that requests are processed quickly and accurately. The ability to effectively manage and process these requests directly impacts business outcomes and a company’s reputation. In today’s competitive environment, organizations that can swiftly address customer data requests and continuously improve their processes gain a competitive advantage, leading to repeat business and stronger customer loyalty.
Managing Large Datasets
For large datasets, use indexing and data partitioning to speed up query performance. For example, indexing by customer_id allows faster data retrieval even for large-scale requests. Analyzing data at this scale provides valuable insights into customer feedback and customer preferences, enabling organizations to enhance their processes.
Enhancing Data Security
To mitigate security risks, enforce strict encryption policies and access controls. Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) should be used to prevent unauthorized data access. These measures also ensure customer satisfaction by safeguarding personal data.
Compliance and Auditing
Maintaining compliance with GDPR, CCPA, and other Data Regulations requires detailed auditing and monitoring systems to safeguard data privacy and protect customer data. With the rise of big data, organizations must leverage advanced technology and data analytics to manage large datasets, ensuring that every aspect of data management is handled effectively. This is essential for delivering an exceptional customer experience and promoting customer loyalty.

Auditing systems must provide insights into customer behavior, enabling organizations to analyze customer data and extract valuable customer insights to enhance marketing strategies and create personalized promotions. The ability to track historical data and segment customers by their preferences allows for more targeted and practical approaches that directly influence business outcomes and drive repeat business.
The continuous improvement of business operations through data auditing enhances business value, supports business strategies, and strengthens a company’s reputation. In the competitive retail industry, staying compliant with regulations and maintaining accurate records not only ensures legal compliance but also provides a competitive advantage. By consistently reviewing and refining compliance procedures, companies can leverage machine learning and artificial intelligence to improve the accuracy of their systems, resulting in more efficient and secure data management.
Pandectes GDPR Compliance App for Shopify
Pandectes GDPR Compliance app plays a crucial role in this process by providing organizations with tools to ensure compliance while managing customer data responsibly. Implementing Pandectes GDPR enables businesses to simplify auditing, ensure transparency, and maintain robust compliance with data protection regulations like GDPR and CCPA. Pandectes also supports CCPA (California Consumer Privacy Act) compliance, ensuring that businesses meet the requirements for handling consumer data in California.
Audit Logs and Real-Time Monitoring
Every action taken on customer data, from access to deletion, should be logged for auditing. Using tools like Elasticsearch or Splunk, organizations can monitor logs in real time and generate reports for compliance audits.
Conclusion
Finally, building trust with your customers is essential, and GDPR-compliant data management plays a key role in this. Handling customer data requests in line with GDPR regulations can be challenging, but with the right tools, like the Pandectes GDPR Compliance App for Shopify, businesses can automate processes, enhance data security, and ensure scalability. Pandectes helps you manage customer data requests efficiently while keeping your business compliant with GDPR and CCPA regulations. By implementing Pandectes, businesses not only mitigate risks but also build a foundation of trust, ensuring customer loyalty, improving customer experience, and enabling personalized promotions. Invest in a comprehensive compliance solution today to protect your business and customers’ data effectively.
Key takeaways:
Automate processes to handle requests efficiently.
Implement robust data security measures.
Ensure compliance through auditing and logging.
FAQs
1. How long does an organization have to respond to a data request?
Organizations typically have one month to respond under GDPR.
2. What is the “Right to Be Forgotten”?
It is the right of individuals to request that their data be deleted from an organization’s systems.
3. How can I ensure data security during a request?
You can protect personal data during the request process by implementing encryption, RBAC, and MFA.